There are many types of proxy servers. These types can be grouped by protocol, number of active users (shared proxies, private proxies, and virgin proxies), the type of IP address assigned (public or free proxies, residential proxies, mobile proxies, and data center proxies), and the IP version (IPv4 and IPv6 proxies). This article, however, shall focus on HTTP and HTTPS proxies, which fall under the proxy by protocol category.
But first, let us discuss the protocols on which HTTP proxies and HTTPS proxies are based.
Understanding HTTP and HTTPS
What is HTTP?
The Hypertext Transfer Protocol or HTTP is a stateless, application-level protocol that facilitates communication between client applications (such as web browsers and web apps) and web servers (or web user interface servers).
It is a layer 7 protocol (or application layer protocol), meaning it is meant to transmit data between the server and client and vice versa. HTTP generally supports the transmission of a variety of data types. These include text, video, and audio data, collectively known as hypermedia.
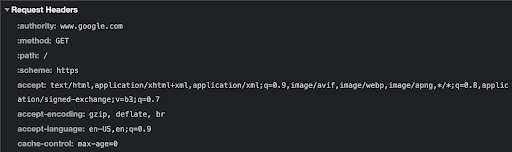
When a client wants access to this data, which is stored on a server, it sends an HTTP request. Generally, the HTTP request contains the following:
- A request line that specifies the HTTP method (GET, POST, PUT, DELETE, and so on), HTTP version (below), and additional information about the request’s target (hostname and port)
- Headers, which store additional information, e.g., cookies
- Body of the request message
Upon receiving the request and interpreting the message, the server then sends an HTTP response containing the requested data.
How Does HTTP Work?
It is worth pointing out that HTTP does not perform its functions in isolation. In fact, it runs on top of transport layer protocols (layer 4), such as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). Furthermore, it was also built over the IP protocol, which existed at the time.
On their part, these layer 4 protocols establish, manage, and close communication between a server and a client (networked devices). To put it simply, TCP and UDP allow networking applications, which sit above the fourth layer (including applications that use HTTP), to create client-server or point-to-point communication with each other.
Once the communication is established, HTTP now swings into action to transmit the data. The TCP or UDP manages the communication by ensuring it runs smoothly, and once the data transmission ceases, these layer 4 protocols close the communication. Notably, TCP and UDP use port numbers to identify the web applications that are ‘talking’ with each other. Another point of note is that the implementation of HTTP/3, the latest version, uses QUIC instead of TCP for the transport layer aspect of communication. (QUIC is a multiplexed transport protocol implemented on UDP.)
History of HTTP
HTTP was first released in 1991 following about two years of development by Tim Berners-Lee and his team. Since then, the protocol has undergone an evolution that has seen numerous changes and improvements, leading to several HTTP versions. These versions include:
- HTTP/0.9 (introduced in 1991)
- HTTP/1.0 (standardized in 1996)
- HTTP/1.1 (introduced and standardized in 1997)
- HTTP/2 (standardized in 2015)
- HTTP/3 (introduced in 2022)
What is HTTPS?
While HTTP is a popular protocol that is widely used on the internet, it has a few shortfalls, chief among them security. With HTTP, all information is transmitted in clear text. It can, therefore, be easily viewed by attackers. It can, in fact, be concerning if the data contains sensitive data such as credit card information, passwords, usernames, phone numbers, social security numbers, address details, and more. To solve the security conundrum, HTTPS was introduced.
Hypertext Transfer Protocol Secure (HTTPS) is a secure HTTP protocol that encrypts all data transmitted via HTTP. HTTPS uses either the Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocol to validate the identity of the web server and protect the data. The SSL uses keys (public and private keys) and digital certificates to secure the data, while TLS relies on cryptography to encrypt the data. TLS also authenticates both the client and server.
History of HTTPS
HTTPS was created in 1994. At that time, it primarily used SSL. However, later in 2000, HTTPS that uses TLS was standardized. According to observers, it has taken years for TLS to become widely used outside of credit card payments. This is particularly because TLS certificates require additional technical knowledge to install and cost money. As a result, they were not feasible, especially for smaller sites. But the landscape has changed, with web hosting services and cloud companies launching free encryption certificate programs and offering HTTPS for free. By 2017, half of the web was encrypted.
With the basics out of the way, let us now focus on what an HTTP proxy is and what an HTTPS proxy is, their similarities and differences, and their uses.
What is an HTTP Proxy?
Before explaining what an HTTP proxy is, let’s first understand what is a proxy server. A proxy server or proxy is an intermediary that sits between a web client and a web server. It works by routing internet traffic through itself and, in the process, acts as the originator of requests and terminator of responses. Generally, there are a number of proxy servers, each designed to serve a specific function.
In fact, there are proxies configured to act on behalf of the client such that they are perceived as the originators of requests and terminators of responses. Such proxies are known as forward proxies. On the other hand, some proxies can be configured to act on behalf of the server. In executing this role, they appear to be the point at which the requests terminate and the responses originate. Such proxies are known as reverse proxies. Incidentally, HTTP proxies can act as either forward proxies or reverse proxies, depending on the location at which the configuration occurs.
So, what is an HTTP proxy server? It is a proxy server that only routes HTTP traffic through itself. The HTTP proxy is a type of protocol-based proxy alongside SOCKS5 proxies. However, unlike the SOCKS5 proxy, which is essentially meant to facilitate communication through a firewall, the HTTP proxy is intended to act as a high-performance content filter.
The HTTP proxy normally listens to HTTP traffic through ports 80, 8080, 8008, and 3128. It can also listen to HTTPS traffic via port 3129. While it is mostly used in isolation, you can connect it to an existing proxy, particularly if the application you are configuring is already using a proxy server. This arrangement creates a chained proxy.
Types of HTTP Proxies
There are two types of HTTP proxies, namely:
1. HTTP Client Proxy
Typically, an HTTP client proxy forward requests to itself (as an intermediary) before forwarding them to a server or target destination. It, therefore, appears as the originator of the requests.
An HTTP client proxy routes all outgoing HTTP requests and incoming HTTP responses through itself. In the process, it interprets all the contents of the HTTP request and response. It can also change certain contents of the HTTP request as long as they conform to the Guidelines for Web Content Transformation Proxies. Generally, HTTP client proxies change specific HTTP headers, including user-agent, accept, accept-charset, accept-encoding, accept-language, x-forwarded-for, and via. It can also convert the request method from HEAD to GET and vice versa.
Configuring your system and, by extension, web browser to use an HTTP client proxy (more on this below) does a few things. First, it changes the TCP endpoint (port and hostname) in the HTTP URLs to the one that belongs to the HTTP proxy provider. As a result, a TCP connection is first made to a different port and host (the proxy’s port and host) other than the one in the HTTP URLs before being sent to the original/real host and port. This is because the proxy does not alter the contents of the message, which contains the real host and port. As a result, an HTTP proxy can receive requests on a single port before then forwarding the requests and the messages therein to different servers and websites based on the destination data contained in the HTTP messages.
2. HTTP Server Proxy
In some cases, some applications, such as those found on a web server, cannot be configured as originators and instead have to be configured as endpoints. As a result, they appear to web clients as the destination of the requests. When these applications are configured as endpoints, they are known as HTTP server proxies.
Types of HTTP Proxies Ranked by Anonymity
HTTP proxies differ in the degree of anonymity. The following types of HTTP proxies can be distinguished:
- Transparent proxies: With transparent proxies, the user usually does not notice that he is using a proxy connection. The proxy connection is only visible to the website operator or service provider. The main advantage of transparent proxies is that they increase the connection speed by caching data.
- Anonymous proxies: With anonymous proxies your IP address is hidden. In this case, the target website can see that you are using a proxy, but not your actual IP address.
- Distorting proxies: A proxy server of this type can be identified as a proxy by a target web site, but will communicate an incorrect IP address.
- Elite Proxies: These are anonymous proxies that delete user data before the proxy attempts to connect to the target website. With these types of proxies, the target website cannot detect that a proxy is being used, nor can it identify the user’s IP address.
All reputable proxy providers that have HTTP proxies offer only elite proxies.
How to Set Up an HTTP Proxy
This section will primarily focus on how to create an HTTP client proxy. It is created by configuring a web client (browser) to route HTTP traffic through an intermediary. However, it is worth noting that Chrome, Safari, Mozilla Firefox, and other popular browsers do not have in-app (native) proxy server settings.
Instead, when you click on the program’s settings and choose the proxy option, it redirects you to the Windows, macOS, or Linux proxy configuration window. In this regard, to create an HTTP proxy, simply configure your operating system. Doing so will create a system-wide HTTP proxy that works with all other web apps, not just your preferred browser.
To set up an HTTP proxy on Windows, follow the procedure below:
- Open Windows’ Settings > Select Network & Internet > Choose the Proxy tab. Alternatively, you can use your browser to open the Proxy tab.
- Head to the Manual proxy setup section
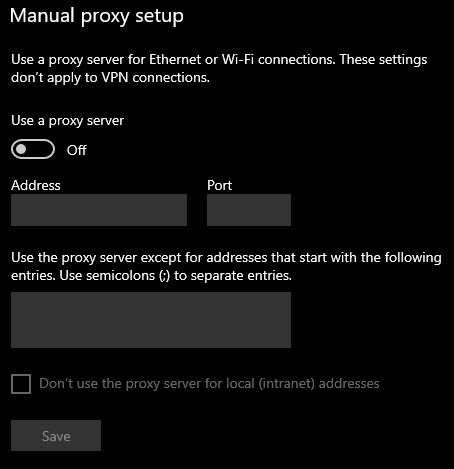
- On the address field, enter the IP or address of the proxy host. In addition, enter the proxy port. Your proxy provider should furnish you with the details.
- Under the ‘Use the proxy server except for addresses that start with the following entries’ box, enter the URL of your proxy service provider
- Next, check the Don’t use the proxy server for local (intranet) addresses
- Click Save
To set up an HTTP proxy on macOS, here are the steps to follow:
- Click System Preferences > Choose Network > Click on Advanced > Select the Proxies tab. Alternatively, you can use your web client, which will automatically open the Proxies tab
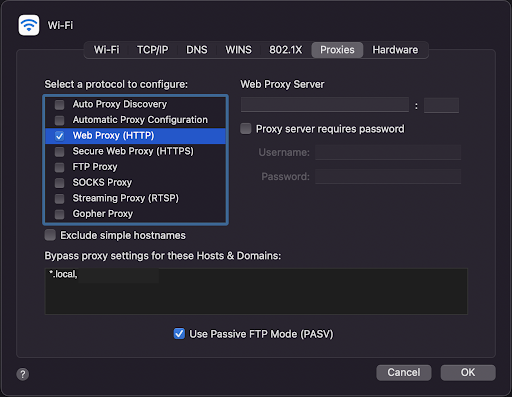
- Next, toggle the Web Proxy (HTTP) option
- Enter the IP and port of the Web Server Proxy (HTTP proxy). Typically, you should enter your proxy service provider’s IP and enter ports 80, 8080, or 8008 in the field.
- Key in the username and password of the HTTP proxy. The username and password should be the same as the credentials you use to access the account you have with your service provider.
- Click OK.
If security is a central consideration when browsing the web, then the HTTP proxy is not ideal. What you would ideally be looking for is an HTTPS proxy.
What is an HTTPS Proxy?
Also known as an SSL proxy, an HTTPS proxy is an intermediary that only listens to HTTPS traffic on port 443. As a result, it only routes HTTPS traffic through itself. As stated above, HTTPS encrypts the data transmitted through the protocol. This effectively means that all elements of the HTTP requests and responses, including the headers and messages, are hidden behind a cryptographic key. Therefore, they can only be viewed or interpreted at the endpoint or point of termination. For an intermediary, such as an HTTPS proxy, to interpret the data, it must be configured as an endpoint.
In this regard, an HTTPS proxy is configured to act as an endpoint of a TLS or SSL connection. It, therefore, decrypts the requests, interprets the contents, changes certain aspects of the requests, encrypts them, and, finally, forwards them to the real destination contained in the HTTP message. As stated earlier, the HTTPS protocol uses certificates. Accordingly, the HTTPS proxy must encrypt the traffic with the correct certificate (either client or server certificate) before sending it to the intended destination. Notably, if the HTTPS proxy is not configured as an endpoint, it should not alter the contents of the HTTP header or request, as stipulated by the Guidelines for Web Content Transformation Proxies.
HTTPS proxies are generally used to secure web servers or web clients by performing encryption.
Types of HTTPS Proxy
There are two types of HTTPS proxies:
1. HTTPS Client Proxy
An HTTPS client proxy facilitates connections from a web client or internal network to the internet. To set up an HTTPS client proxy, you must import a client certificate for use by the device on which the proxy is installed. This enables the intermediary to both decrypt and encrypt data as if it were the originator of the requests or terminator of the responses.
2. HTTPS Server Proxy
An HTTPS server proxy allows connections from external web clients to internal web servers via the internet. An HTTPS server proxy differs from an HTTP server proxy because the former utilizes certificates, while the latter does not. To set up an HTTPS server proxy, it is important to export the default certificate used by your web server to the proxy. The certificate enables the HTTPS server proxy to encrypt and decrypt the data.
How to Set Up an HTTPS Proxy
Setting up an HTTPS proxy follows the procedures detailed above, with only slight differences around the ports used. Always ensure you have entered 443 within the port field every time you are creating an HTTPS proxy. If you are using a macOS device, do note that you must select the Secure Web Proxy (HTTPS) option instead of Web Proxy (HTTP). Otherwise, the procedure is largely the same.
How Secure is a Connection Through an HTTPS Proxy?
When a user using an HTTPS proxy opens a web page with a “lock icon” to the left of the address bar, the entire connection between the user’s browser and the server of the target site is encrypted (SSL encryption):
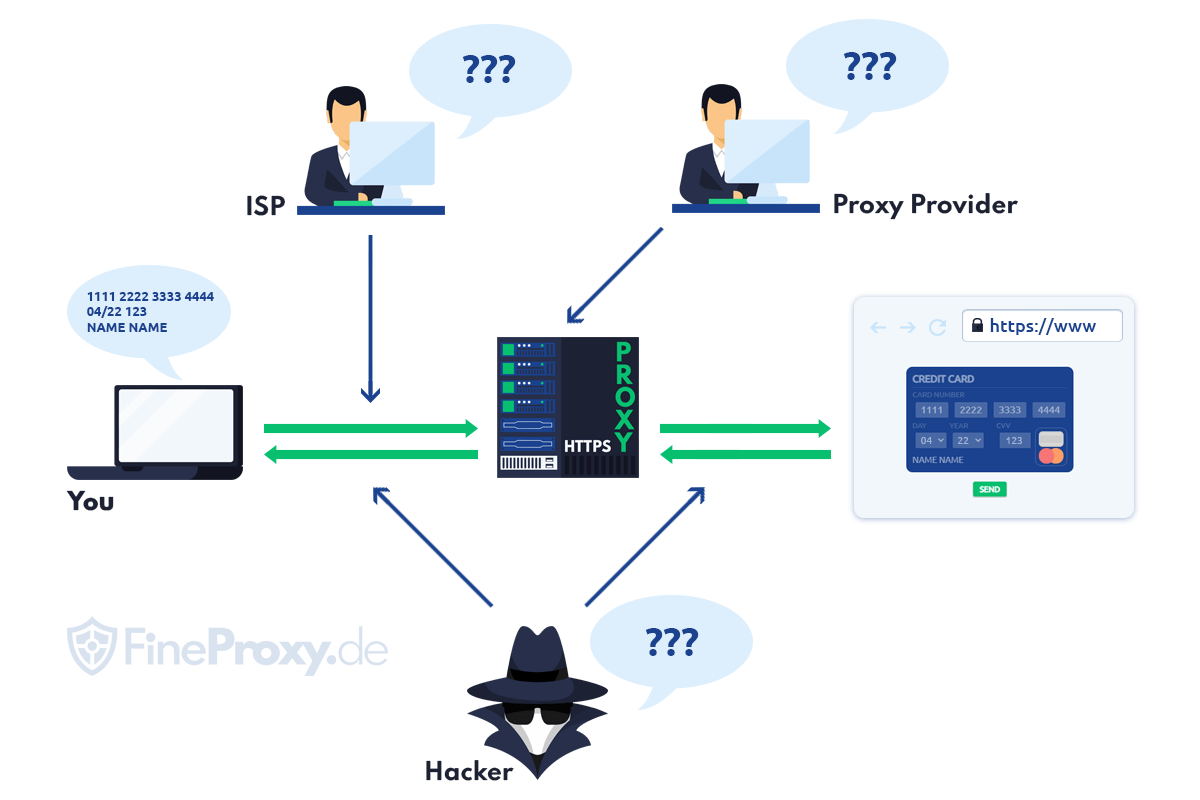
This means that all data entered by the user on the keyboard (logins and passwords, credit card numbers, etc.), images, and videos downloaded, uploaded, or streamed remain absolutely private.
Browser <- > HTTPS-Proxy <-> Target page
This means that they are known only to the user and the owner of the target website.
Can the Proxy Service “Listen” to the Traffic?
No, this is technically impossible. The proxy provider can only guess that the user is trying to hack passwords to accounts on any website. This is apparent from the frequency of access to the login page of the target site. This will occur if the user does this at a frequency of one million times per minute using a brute force program.
HTTP Proxies vs. HTTPS Proxies: Similarities and Differences
Similarities Between HTTP and HTTPS Proxies
- They can be configured on either the client-side or server-side
- HTTP and HTTPS proxies interpret the data transmitted through them
- The proxies listen to traffic via ports
- Client-side proxies forward all requests to the target destination
- Client-side proxies can be used to facilitate web scraping
Differences Between HTTP and HTTPS Proxies
| HTTP Proxies | HTTPS Proxies | |
| Ports | They use ports 80, 8080, 8008, 3128, or 3129 | They use port 443 |
| Security | HTTP proxies route unencrypted data | HTTPS proxies route encrypted data |
| Protocol | They mainly use the HTTP protocol | They primarily use the HTTPS protocol |
| Traffic | They can listen to both HTTP (via ports 80, 8080, 8008, 3128) and HTTPS traffic (via port 3129) | They can only listen to HTTPS traffic via port 443 |
Uses of HTTP and HTTPS Proxies
Uses of HTTP Client Proxies and HTTPS Client Proxies
1. Web Scraping
Web scraping refers to the automated process of extracting data from websites using bots known as web scrapers. Ordinarily, these bots are designed to extract large volumes of data, which can strain web servers by unnecessarily usurping resources. For this reason, most large websites are now implementing anti-scraping measures aimed at stopping any data extraction efforts. Fortunately, you can get around this problem using HTTP proxies.
HTTP proxies are mostly overlooked when it comes to data extraction. This is because residential proxies, mobile proxies, or data center proxies are preferred as they mask the IP address of the computer on which the scraper is running. It simultaneously assigns a different IP address, effectively providing online anonymity. Additionally, it protects the real IP address from getting blocked or banned. If the IP address is rotated periodically, the chances of blocking are further reduced. But this article isn’t about residential or data center proxies. So, how are HTTP proxies and HTTPS proxies used in web scraping?
As stated, an HTTP or HTTPS proxy can change some HTTP request headers. These include the user-agent, accept-language, accept-encoding, and accept, just to mention a few. The user-agent stores information about your operating system (type and version), the client application in use (web browser), and the browser engine. This information allows a web server to identify the type of device and software used to access it. It then uses this information to create an online identity associated with the user. By altering the user-agent, an HTTP proxy and HTTPS proxy can make it appear as though the requests are originating from different devices. This boosts web scraping, as the data extraction requests appear to have been sent by multiple devices.
2. Content Filtration
An HTTP client proxy or HTTPS client proxy can be configured to forward only specific requests – such requests must fulfill certain rules. For instance, they must be sent through specified ports. Access is denied if the HTTP client uses a port other than 80, 8080, 8008, 3128, or 3129.
Additionally, you have to specify the types of content the HTTPS or HTTP proxy should look at as it examines traffic to and from a client. The traffic is blocked if the content does not match the criteria specified in the settings. Conversely, if the content matches, then it is allowed to pass through the intermediary.
3. Securing Communication
An HTTP proxy can be configured to convert the inbound data from plain text to secure, encrypted outbound data that can be accepted by HTTPS servers. However, this configuration is unusual, but it involves the use of port 3130, which is the port that handles plain text to SSL communication.
On the other hand, HTTPS proxies secure communication by encrypting it. In this way, HTTPS proxies promote cybersecurity, as they reduce the chances of cyberattacks.
4. Social Media Management
By now, it is common knowledge that HTTP proxies modify some aspects of the HTTP header. Thus, by changing the user-agent, these intermediaries can create the illusion that the requests are originating from different devices. This can allow users to create and manage multiple social media accounts.
Uses of HTTP Server Proxies and HTTPS Server Proxies
1. Limiting Traffic to Web Server
The server-side proxies can be configured to accept traffic that fulfills certain rules. As such, they block traffic that does not conform to the requirements. This way, they protect the server by ensuring it does not process unnecessary requests.
2. Securing the Web Server
The server-side proxies can decrypt the data from web clients and subsequently interpret them. This action enables them to filter the requests, scanning them for malware or other malicious files. As a result, they safeguard the web server against cyberattacks.
3. Caching Frequently Accessed Files
HTTP server proxies and HTTPS server proxies can store frequently accessed files such as images and pages. This frees up the web server, enabling it to dedicate resources to other less common operations. It also increases the loading speed of web pages.
Conclusion
HTTP proxies and HTTPS proxies are useful intermediaries, particularly from a security and content filtering perspective. In fact, they are referred to as high-performance content filters. This is because they can be configured to allow only specific internet traffic to pass through. These proxies also serve numerous other functions, including securing web servers, storing frequently accessed files, social media management, web scraping, and more.