Did you know that each time you connect to public Wi-Fi, you’re engaging with an invisible digital mediator? Meet the transparent proxy, a behind-the-scenes web traffic manager that seamlessly filters, validates, and stores your online requests without tinkering with your IP address. Remarkably undetectable, this silent enabler performs its functions without any configuration on your part, leaving you free to surf the internet uninterrupted.
Join us in this intriguing journey as we unravel the functionalities, business applications, and detection methods.
Table of Contents
- What is a Transparent Proxy?
- Transparent Proxies and Forced Proxies
- Transparent Proxy Settings
- How Does a Transparent Proxy Work?
- Uses for Transparent Proxy
- Advantages and Disadvantages of Transparent Proxies
- How to Detect a Transparent Proxy?
- Transparent Proxy vs. Non-Transparent Proxy
- VPNs and HTTPS vs Transparent Proxies
- How to Set Up a Transparent HTTP+HTTPS Proxyserver Using Squid and IPtables
- Conclusion
What is a Transparent Proxy?
Transparent proxies are also known as inline, intercepting, or forced proxies. These intriguing servers cleverly intercept connections between end-users or devices and the internet while remaining “transparent.” This means they operate without meddling in requests and responses. One well-known open-source transparent proxy tool is the Squid Transparent Proxy Server.
Picture this: a user at work browses the internet and decides to read a news article on cnn.com. Thanks to the transparent proxy, this user will see the exact same content as they would at home. How amazing, right?
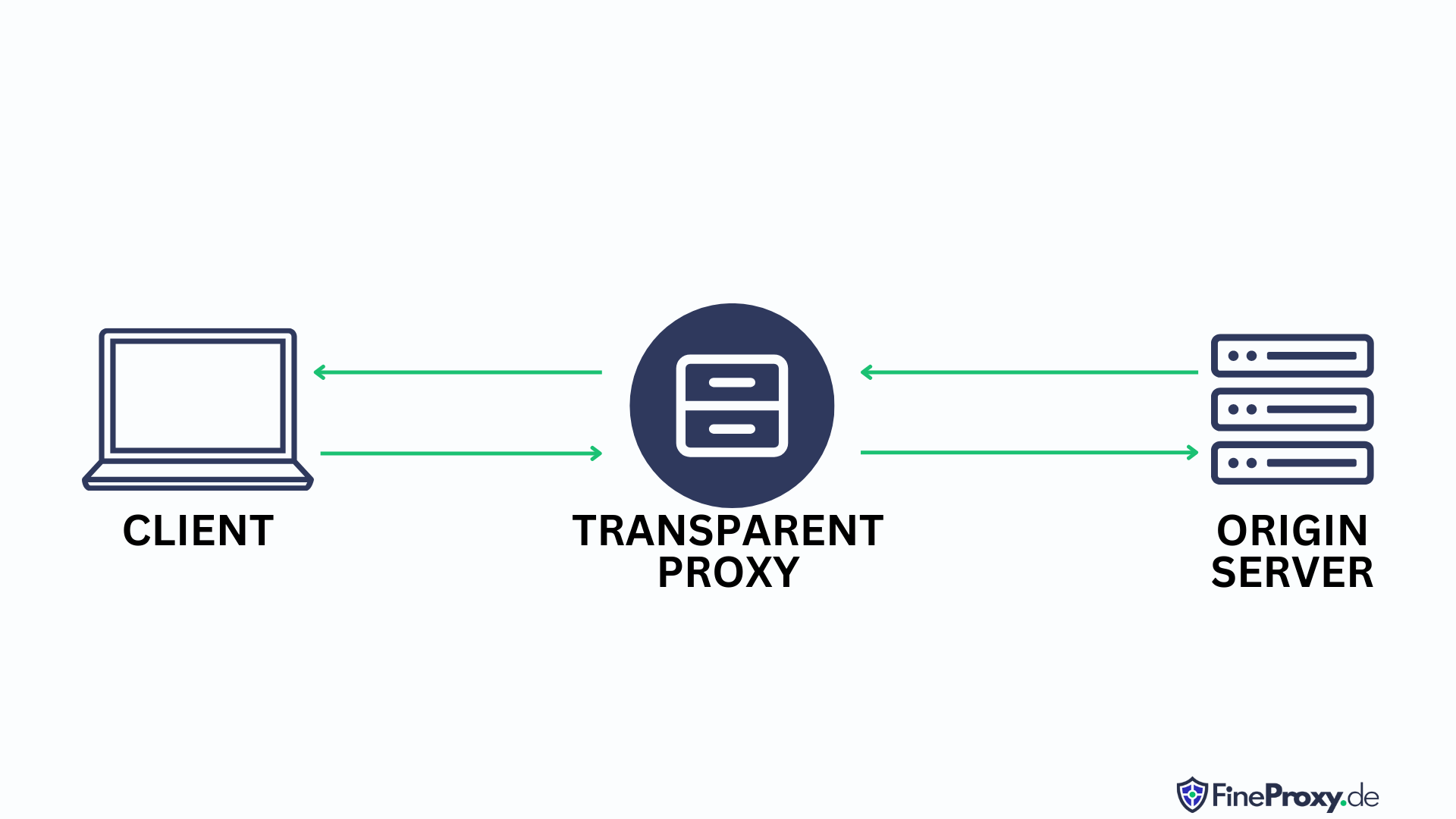
Imagine browsing the internet, reading a captivating news article from cnn.com, all while thinking your browsing habits are private. Little did you know, your employer stealthily monitors your actions, thanks to a discreet proxy on the corporate network. Though the experience seems unchanged, your employer wields power to watch your online behavior and even limit access to specific sites.
Transparent Proxies and Forced Proxies
Transparent proxies are also known as forced proxies, as they seamlessly integrate into a user’s connection without tinkering with their computer’s proxy settings. This unique feature enables network operators and website owners to implement them without users’ permission or awareness. As a result, a transparent proxy can be “forced” on a user without their consent or knowledge (although in many cases, users are informed about the presence of a proxy).
However, fret not – numerous websites provide unsanctioned transparent proxy lists to keep users informed about their monitored status.
Transparent proxies, by definition, are set up by the operator of a network or a website, and not by the end-user.
Transparent Proxy Settings
Discover the exciting world of transparent proxies and master their common settings, such as:
- Remarkable authentication that seamlessly links server credentials with users behind the scene.
- Intriguing interception methods, customizable at either the operating system or router level.
- Unprecedented caching capabilities for an enhanced experience for returning users.
- The astonishing reverse proxy option is designed to boost performance while placed in front of a web server.
- Superior filtering mechanics expertly restrict access to specific protocols or ports, like chat services, data streaming, and torrent threads.
How Does a Transparent Proxy Work?
Picture a secret doorperson, dutifully and discreetly handling your internet inquiries. Welcome to the world of transparent proxies! As you send a request online, this cyber-gatekeeper takes your private IP address and transforms it into a public one before forwarding it to your intended destination. And to ensure you receive the coveted response, the proxy memorizes your private IP address, recognizing the incoming answer as yours to complete the communication circle.
Accessing this digital intermediary is a breeze, typically through dedicated software or a handy browser extension.
In contrast to regular proxies, transparent proxies mask their presence from the client and do not manipulate any of the data being sent through them. As a result, requesters will remain oblivious to this kind of proxy as requests appear to originate with the user instead of coming from an intermediary device on the network.
Uses for Transparent Proxy
You can deploy a transparent proxy on the client side, meaning that all traffic to and from a client endpoint is intercepted by the proxy.
On Client Side
Use cases for client-side transparent proxies include:
Content Filtering
The power of a transparent proxy is to efficiently filter unwanted content through customizable proxy settings. Imagine a situation where a particular website is accessed, and instead of forwarding the request, the proxy cleverly intercepts the connection, presenting an error or informative notice to the user.
Gateway Proxies
The synergy of a gateway proxy that seamlessly modifies or obstructs network traffic according to predefined rules. Picture a firewall operating as a transparent proxy, permitting traffic to flow between an internal network and the Internet, while swiftly blocking any traffic that infringes upon its rule table.
Transparent Caching
Imagine a bustling university campus where numerous students eagerly peruse the same trending news site. To optimize their browsing experience, a transparent proxy springs into action, cleverly caching the content to swiftly serve it up for subsequent users. This digital hero not only enhances efficiency but also unites organizations, facilities, and neighborhoods in the quest for seamless connectivity.
Traffic Monitoring
One of the main uses of transparent proxies is for an insightful analysis of user traffic and behavior on your network while remaining vigilant against potential misuses such as data theft and credential breaches by unsavory public Wi-Fi operators.
Authentication
You may use the intrigue of public Wi-Fi spots and cellular internet providers employing hidden forces, like transparent proxies, to gently coerce users into authenticating on networks and pledging agreement to terms of service. Discover the secret behind the continued surveillance of connections, even after gaining access, as the operator stealthily monitors the user’s every move through the unseen eyes of the transparent proxy.
On the Server Side
Use cases for server-side transparent proxies include:
TCP Intercept for DoS Protection
Enter TCP intercept, a powerful transparent proxy with the ability to outsmart SYN-flood attacks. Acting as a trusted intermediary, this robust proxy skillfully handles incoming client requests, navigates through the three-way handshake process, and seamlessly links both client and server endpoints.
What sets TCP intercept apart is its vigilant observation of TCP requests and its ability to adapt when it detects trouble. By monitoring connection durations and employing a 30-second wait time in normal circumstances, TCP intercept ensures only legitimate connections can communicate with your server. But when the number of inactive connections crosses a predetermined limit, the proxy springs into “aggressive mode,” swiftly eliminating the oldest inactive connection for every new one that arrives. Equip your server with TCP intercept and breathe easy knowing your online fortress has an ever-watchful guardian.
In today’s hyperconnected landscape, traditional defenses can no longer hold their ground against massive Distributed Denial of Service (DDoS) onslaughts. Cyber adversaries armed with formidable server power and armies of undead computers can generate titanic SYN floods, easily rending apart TCP intercept controllers.
Enter the epoch of cloud-based fortifications like Imperva’s DDoS Protection: born to stand tall even in the face of the fiercest DDoS tempests. These vigilant guardians swiftly scale to colossal levels, cloaking the realm from not only TCP, but also protocol and application layer attacks. Dawn a new era of digital security by embracing the supremacy of cloud-based DDoS services.
Transparent Proxy and CDN for Front-End Optimization
You’ll get lightning-fast browsing with Content Delivery Networks (CDNs), a magnificent ensemble of proxy servers spread across the globe, designed to serve content at the speed of light to users from nearby locations. A prime example of a seamless CDN is Imperva’s Global Content Delivery Network, which acts as an invisible powerhouse on the server end, focusing on front-end optimization to enhance user experience.
As users cruise through the internet, they never have direct contact with the core server; instead, they’re treated to cached content through these CDNs, leading to awe-inspiring performance and minimal demand on the server’s resources. Harness the power of a CDN for an unmatched browsing experience!
Advantages and Disadvantages of Transparent Proxies
Like any other online tool, transparent proxies come with baggage – a list of advantages and disadvantages. Here are some of them:
Advantages:
- These savvy tools elevate loading speeds and conserve upstream bandwidth for ultimate efficiency.
- Best of all, implementation is a breeze – well-known tools, like the Squid Transparent Proxy Server, make setup quick and seamless. Say goodbye to burdensome system reconfiguration and hello to smooth network rerouting for multiple clients.
- Even during overloads or crashes, transparent proxies outshine their explicit counterparts, thanks to their built-in interception element dedicated to swift troubleshooting and problem resolution. Stay ahead of the game with the unbeatable performance and ease of use that transparent proxies offer.
Disadvantages:
- There are some architectural challenges and network perils of transparent proxies, which demand a keen understanding of client-side modifications and rely heavily on compatible server operating systems and devices.
- Beware of the pitfalls associated with improper configurations, as they can lead to a sluggish network and unstable connections.
- Moreover, ensuring data security is an arduous task, where the right protocol selection can make or break your defense against malicious attacks and data breaches. Trust only the experts, for the stakes are high and the consequences, grave.
How to Detect a Transparent Proxy?
Unbeknownst to some, transparent proxies have become increasingly commonplace in digital networks, and it may be difficult for the average person to tell if their web requests are routed through one.
Fortunately, there are a few measures that can assist with this verification process. For instance, HTTP response headers obtained from websites should display X-Forwarded-For or Via as an indicator of proxy use within these responses; alternatively, users could resort to using specialized online tools specifically tailored towards proxy detection purposes – easily accessible via any search engine.
Transparent Proxy vs. Non-Transparent Proxy
While the transparent proxy remains undercover, quietly guiding client requests without detection, its non-transparent counterpart boldly modifies those requests and shields its settings from prying eyes.
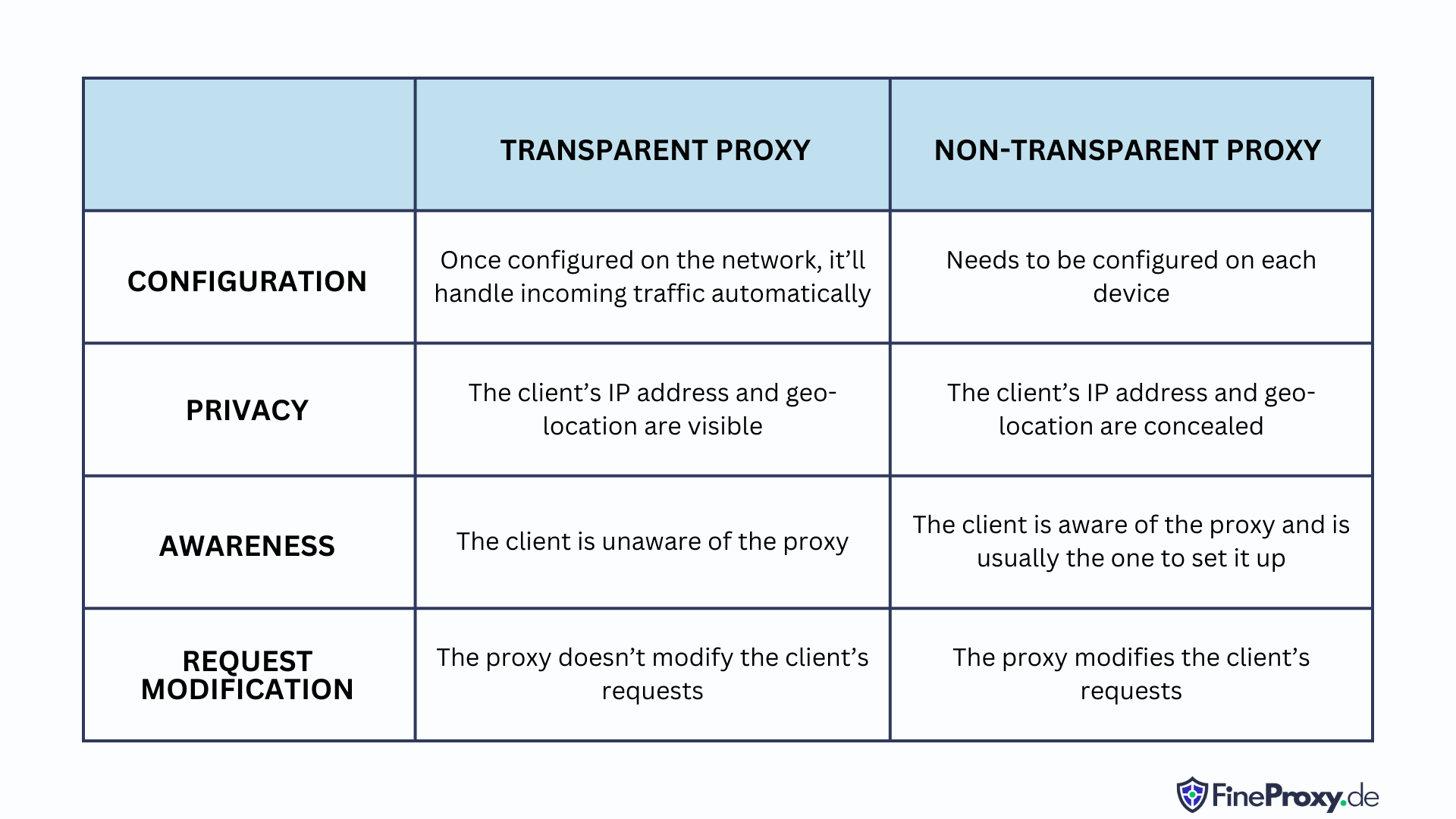
The non-transparent proxy laughs in the face of worms and spyware, providing an unbreachable barrier by concealing its very existence. Imagine a world where these two types guard your digital domain, routing requests through firewalls and leaving clients blissfully unaware of their protective presence.
VPNs and HTTPS vs Transparent Proxies
When browsing online, your data can be sneakily observed and filtered by a mysterious figure called a “transparent proxy.” This master of deception can even store your precious data for its own future agenda.
HTTPS
With its trusty sidekick SSL encryption, HTTPS transforms your regular browser traffic into an unbreakable secret code. It guards your information from any prying eyes and ensures it safely arrives at its destination.
But beware! There is a chink in HTTPS’s armor. DNS traffic, the trusted messenger that reveals the routes of your encrypted data, is often left unprotected. So while the contents remain hidden, the destinations are still visible to potential foes.
Together, HTTPS and DNSSEC (encrypted DNS) can join forces to challenge the transparent proxy and create a truly secure browsing experience. Yet, the compatibility between these champions of privacy can be a rocky affair.
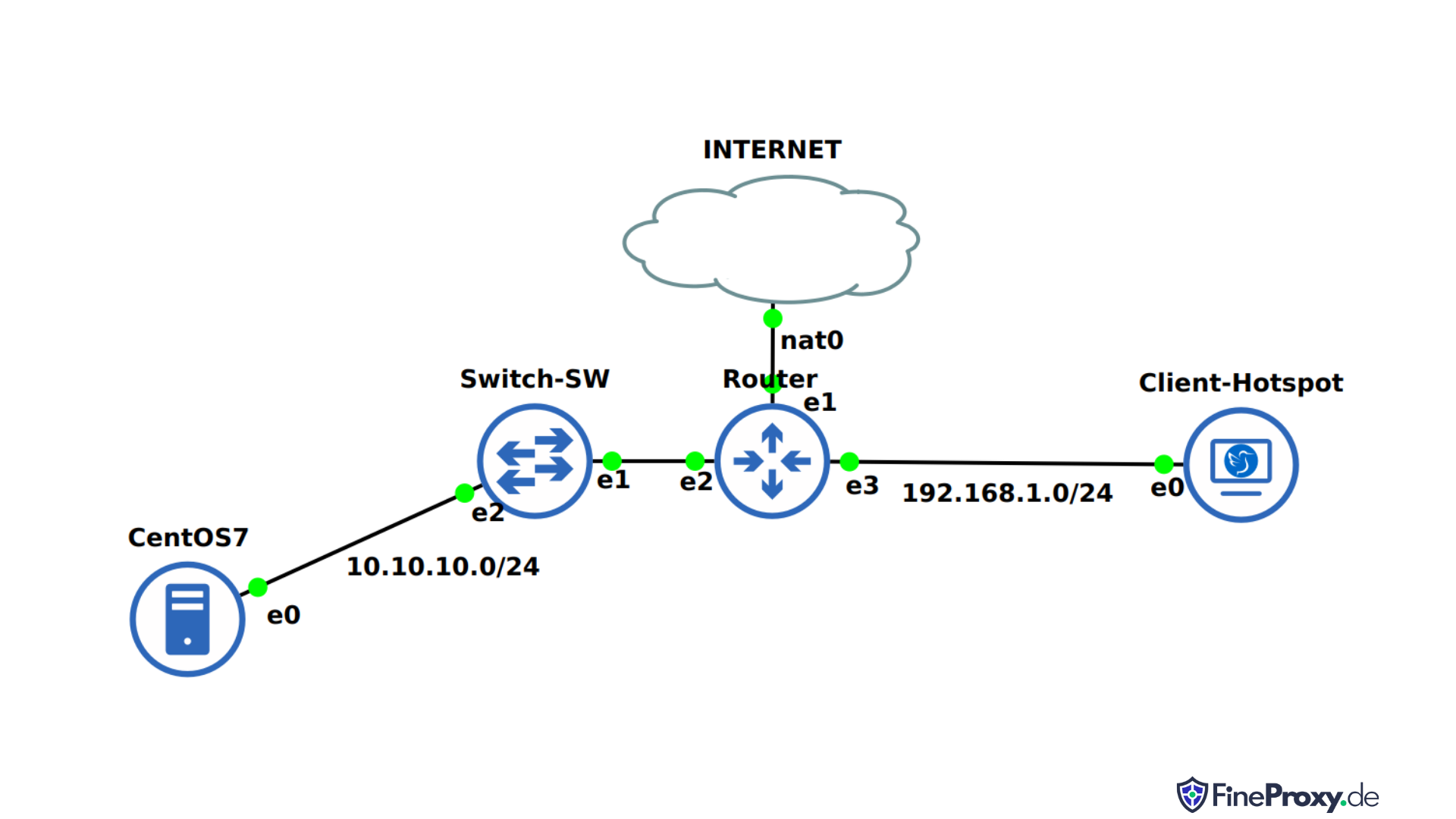
Transparent proxy software, such as Squid, is capable of managing HTTPS traffic in multiple ways. Imagine being able to monitor data destinations seamlessly during transit! Network administrators can even set up HTTPS interception with the proxy server acting as the “man-in-the-middle” with an exclusive HTTPS certificate authority.
VPN
VPNs may provide you with privacy and security by encrypting all data from your device, effectively rendering its contents and destination undecipherable, and allowing for smooth and unaltered transmission to its intended destination. However, be prepared to sacrifice the proxy cache’s speed advantage for the sake of heightened confidentiality.
How to Set Up a Transparent HTTP+HTTPS Proxyserver Using Squid and IPtables
Transparent HTTP+HTTPS Proxying with Squid and iptables provides an efficient way to manage and access online content securely.
By combining Squid and iptables, internet traffic is routed through a secure proxy server, allowing for the filtering of requests, caching of popular objects, as well as providing authentication to users. This combination also allows for the secure transmission of data over both HTTP and HTTPS connections, providing an added layer of protection for your online data.
Additionally, with transparent proxying, users do not need to manually configure their browsers or applications in order to access internet resources through the proxy. This makes it easier for users to access the content they need without having to worry about manually setting up the proxy.
By combining Squid and iptables, you can easily and securely manage your online content without having to worry about the security of your data.
In this video SysEng Quick’ll be setting up a transparent HTTP+HTTPS proxy using Squid and iptables. He wll be forwarding all traffic from port 8080 on our local machine to port 3128 on the proxy server. This will allow us to filter and monitor all traffic going through the proxy server.
Conclusion
The magic of unseen, soundless transparent proxies works wonders in elevating and streamlining online interactions. Their adaptability serves both clients and servers alike, making business smoother and more efficient. By advancing browsing experiences and providing better command over network traffic, these proxies propel companies into an accelerated growth trajectory.