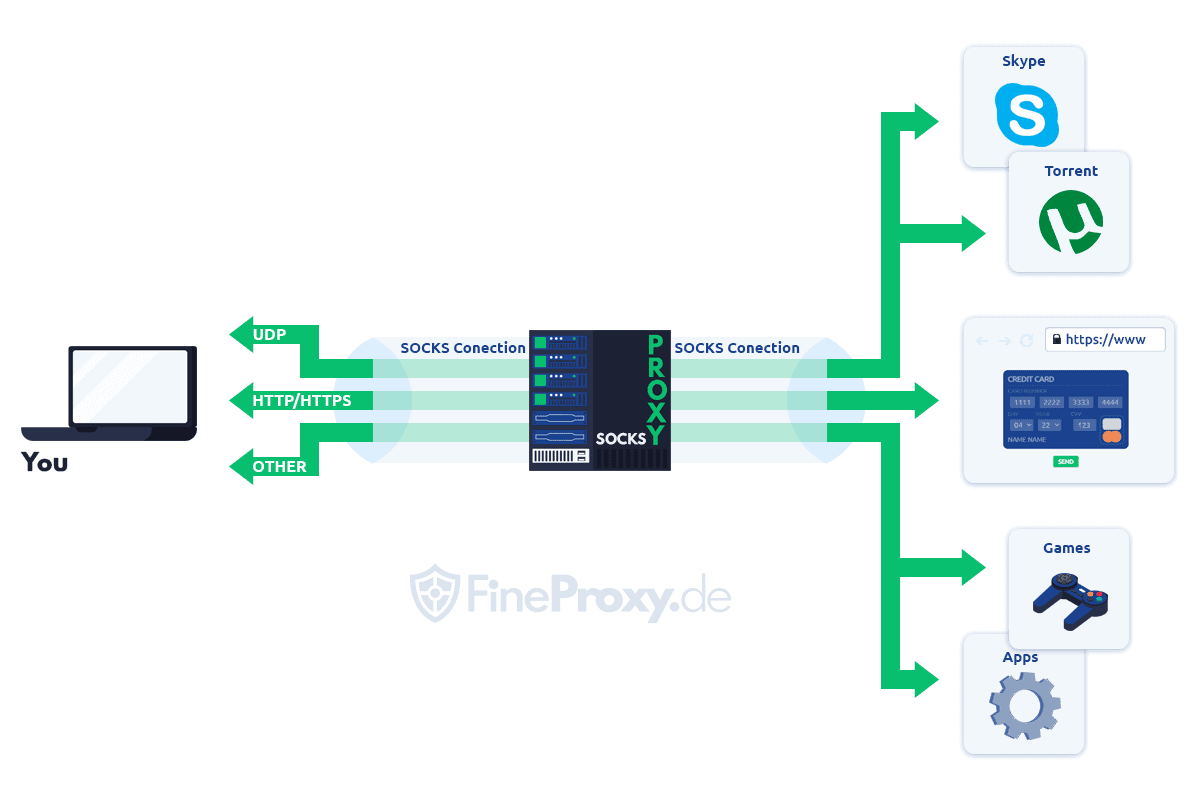
You have likely heard about proxies and perhaps even SOCKS proxies. At their core, proxy servers or proxies are hardware- or software-based intermediaries that sit on a local or remote machine. In this intermediate role, they route all traffic between web browsers (web clients) and web servers through themselves, thus blocking or preventing direct communication.
At the same time, and depending on the type, proxies conceal some information about your online identity. Examples of data concealed include your IP address and location.
Indeed, there are several types of proxies. And they can be broadly categorized into four groups based on the following:
- Protocol, i.e., SOCKS proxies and HTTP and HTTPS proxies
- Number of active users, i.e., shared proxies, private proxies, and virgin proxies
- The direction of traffic routing, i.e., forward proxies and reverse proxies
- The type of IP address assigned, i.e., residential proxies, data center proxies, and mobile proxies
However, this article will mainly focus on proxies identifiable by the protocol used to communicate online. This category includes SOCKS proxies and HTTP and HTTPS proxies.
What Is a SOCKS Proxy Server?
A SOCKS proxy is an intermediary that utilizes the SOCKS protocol to facilitate network connectivity between hosts or between a web client and a web server through a firewall. This proxy runs software known as a SOCKS daemon. The software is specifically installed at a firewall host (machine on which a firewall has been installed), creating a secure route through this firewall.
Therefore, this means the SOCKS protocol does not bypass firewalls but rather allows communication to be routed through the firewall via a proxy server. Accordingly, the firewall blocks all unauthorized traffic as well as traffic that does not conform to certain parameters, such as the username or that which has not been sent using the SOCKS protocol.
However, suppose the communication is sent via this protocol and, by extension, via the SOCKS proxy. In that case, the users will access the internet or be able to communicate with other computers in an external network. Generally, the SOCKS proxy server supports application-level connections, i.e., those sent via application layer protocols, pass. (Application layer protocols include HTTP, HTTPS, SMTP, TELNET, FTP, POP, MIME, and more.)
How a SOCKS Proxy Server Works
As a result of this arrangement, users’ computers, collectively known as hosts, utilize the SOCKS proxy server as a secure transient point that enables secure communication with other hosts or web servers. And given that a network firewall or firewall host still protects the connection through this intermediary, it prevents unwanted intruders from accessing the communication between the hosts. Thus, only parties with accounts on the host (proxy account) can access network packets sent using the SOCKS protocol through the firewall.
The SOCKS proxy server not only enables the communication between users’ computers but also between web clients and web servers. And as is the case with all other proxy servers, it intermediates network traffic, blocking direct access. Thus, when a client sends HTTP, HTTPS, or FTP requests, the SOCKS server receives them and subsequently serves them to the web server on the client’s behalf. At the same time, it receives responses from the server and forwards them to the client. However, before discussing SOCKS proxy servers in greater detail, let’s first understand the SOCKS protocol, its history, and how it works.
History of SOCKS Protocol
The name SOCKS proxy server is derived from a network protocol known as Socket Secure, which is contracted to SOCKS. Based on the above description, the SOCKS protocol provides a framework for network connectivity through a network firewall. The protocol has undergone various improvements since it was first introduced in the early 1990s. And this section will describe the evolution over the years.
SOCKS Version 1
The original SOCKS protocol was proposed in a paper presented at the third USENIX UNIX Security Symposium in 1992. However, at the time of presenting the paper, SOCKS had been running at MIPS Computer Systems for three years. This means SOCKS was originally created on or about 1989.
Authored by David Koblas and Michelle Koblas, the paper discussed how the SOCKS protocol could be used to provide convenient and secure network connectivity through a firewall host. Its creators designed it as a solution to a problem that existed then: the methods of creating a secure environment through that computers could connect to the internet were cumbersome, inconvenient, or could be easily compromised.
The paper presented a SOCKS package, which included the SOCKS library, protocol, and a daemon (SOCKS proxy software). The library included calls that established connections to the SOCKS daemon installed on the firewall. In this way, the library enabled the transmission of information and network connections in such a way that the daemon appeared to be the originator of the requests. Thus, to an external host, the daemon (SOCKS proxy) would appear to be the originator of the requests. The SOCKS library routines or calls included:
- Connect: It requests that the SOCKS proxy (daemon) establishes an outbound connection to a given IP address, port number, and username
- Bind: It requests an inbound connection expected from a given external IP address. It also contains username requirements, but this username belongs to the requestor (sender) and is used for logging the information. Generally, the Bind call binds a new socket connection to a free port on the firewall.
- Listen: It awaits (listens), ready to accept calls from the external host
- GetSOCKName: It gets the IP address and port number of the socket on the firewall
- Accept: It accepts a connection from an external host
SOCKS Version 4 (SOCKS4)
Ying-Da Lee extended the SOCKS protocol, creating SOCKS version 4 (SOCKS4) before later introducing SOCKS version 4a (SOCKS4a). Accordingly, SOCKS4a expanded the protocol’s capabilities by supporting the resolution of the destination host’s (server’s) domain name to find its IP address.
SOCKS Version 5 (SOCKS 5)
In 1996, a group of contributors wrote a memo describing SOCKS version 5. The write-up extended the capabilities of the SOCKS protocol by expanding the capabilities of the underlying framework to enable it to support more sophisticated application layer protocols. Additionally, SOCKS5 introduced support for client-server applications in both the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). Further, it extended the addressing system to include IPv6 addresses and domain-name addressing.
Finally, SOCKS5 introduced strong authentication. The new version specifies a generalized framework for using arbitrary authentication protocols. For example, when initiating a SOCKS connection, the following authentications can be used:
- Username/Password sub-negotiation authentication services (However, the username/password sub-negotiation is unsecured and is, therefore, not recommended in cases where hackers or third parties can undertake ‘sniffing.)
- Secure Username and password authentication that uses known host keys and relays the keys through encrypted communication
- GSS-API authentication method
It is noteworthy that the revisions resulted in several types of SOCKS proxies, namely:
- SOCKS4 proxies
- SOCKS5 proxies
SOCKS4 vs. SOCKS5: Similarities and Differences
Similarities Between SOCKS4 and SOCKS5
SOCKS4 and SOCKS5 protocols and, by extension, proxies are similar in the following ways:
- The SOCKS service in SOCKS4 and SOCKS5 is located on port 1080
- They utilize the same operations, i.e., connect, bind, listen, accept, and getSOCKname.
Differences Between SOCKS4 and SOCKS5
SOCKS4 and SOCKS5 protocols and proxies differ in the various ways described in the table below:
| SOCKS4 | SOCKS5 | |
| Supported Domains | It only supports TCP | It supports both TCP and UDP |
| Security | It provides unsecured firewall traversal because it does not authenticate the network packets | It supports strong authentication schemes, such as username and password requirements, thereby promoting secured firewall traversal |
| Supported Protocols | It supports FTP, SMTP, TELNET, HTTP, and GOPHER (i.e., application-layer protocols) | It supports FTP, SMTP, TELNET, HTTP, and GOPHER, as well as NTP, DHCP, BOOTP, NNP, TFTP, RTSP, RIP, and DNS (i.e., application and transport-layer protocols) |
| IP Address | It supports IPv4 addresses only | It supports IPv4 and IPv6 addresses |
| Domain Name | It is incapable of resolving all domain names and can, therefore, not find their IP addresses | It can resolve all servers’ domain names to find their IP addresses |
| Addressing | It does not support domain-name addressing | It supports domain-name addressing |
How Secure is a SOCKS Proxy Connection?
A SOCKS connection, unlike an HTTPS connection, is not encrypted. But an encrypted HTTPS connection can be established over any SOCKS connection (within the connection), which is completely inaccessible from the outside:
This may look complicated, but in reality, it is very simple, and such a connection is automatically created when the user first establishes a SOCKS connection (e.g. with Proxifier or the browser add-on Foxyproxy) and then goes to a web page that uses an SSL certificate (“lock” to the left of the address bar).
Browser <- > SOCKS (HTTPS ) SOCKS <-> target website
This means that this connection is completely secure, and no one, not even the proxy provider, can find out exactly what the user is doing on the website, what he is printing, what pictures or videos he is viewing or uploading.
Advantages and Disadvantages of SOCKS Proxy Servers
Advantages of SOCKS Proxies
The advantages of SOCKS proxies are:
- Lesser errors: SOCKS proxies, unlike HTTP proxies, do not interpret or rewrite the data packets such as headers. Thus, they are not prone to mislabeling or other errors.
- Support for multiple protocols in the application and transport layers: SOCKS4 proxies support FTP, SMTP, TELNET, HTTP, and GOPHER protocols. In contrast, SOCKS5 proxies support FTP, SMTP, TELNET, HTTP, and GOPHER protocols, as well as NTP, DHCP, BOOTP, NNP, TFTP, RTSP, RIP, and DNS. In contrast, HTTP proxies only support HTTP and HTTPS protocols.
- Better security: SOCKS5 proxies, in particular, undertake authentication at various stages. This promotes security. Generally, however, given that all SOCKS proxies do not interpret or rewrite data, they cannot uncover data packets that contain your personal information.
- Enhanced privacy: SOCKS5 proxies can change your IP address, thus concealing information such as your real location, especially considering that IP addresses store such data.
Disadvantages of SOCKS Proxies
The disadvantages of SOCKS proxies include the following:
- Connection delay/slow speed: SOCKS5 proxies, in particular, have to undertake a number of authentications at different stages of operations, which translates to slower speeds.
- Limited back-connect: The SOCKS5’s bind command does not sufficiently cover protocols that require the server to connect to the client (back-connect) multiple times; instead, it is primarily suitable for protocols such as FTP that require only a single back-connect
- Limited capabilities of supported UDP: SOCKS5’s initial UDP support had limited capabilities. For instance, the protocol envisioned that UDP applications should send data and receive a response. However, many UDP applications can receive UDP data without requiring IP address information, sending data, or using a certain port. Thus, SOCKS5 proxies have limited UDP capabilities.
- Backward incompatibility: SOCKS5 proxies are not backward compatible with the earlier versions of the SOCKS protocol, such as SOCKS4a
How to Use SOCKS Proxies
SOCKS proxies are used in the following ways:
- They allow users to bypass geo-blocking. This way, SOCKS proxies, particularly SOCKS5 proxies, enable them to access content from other locations. (Geo-blocking or geo-restriction is the practice whereby websites only show content to visitors from a specific location.)
- SOCKS proxy servers help bypass internet filtering by schools, workplaces, and governments, just to mention a few
- Anonymous use of messengers, such as Telegram
- Video streaming and live calls
- Torrenting or peer-to-peer sharing and downloading
- Bulk and secure emailing due to SMTP support
- General web browsing because SOCKS5 supports a number of application-level protocols
- Blocking unauthorized access to business networks: SOCKS proxies act as a transient intermediary that enables secure internet access through the business firewall while preventing unwanted intruders from accessing the server or computers within the local network.
SOCKS Proxies vs. HTTP Proxies
As detailed earlier, SOCKS proxies and HTTP proxies are protocol-based proxy servers. For a detailed discussion of what HTTP and HTTPS proxies can achieve, refer to our article on HTTP and HTTPS proxies.
How SOCKS Proxies and HTTP Proxies Compare
This section details the similarities and differences between SOCKS and HTTP proxies.
Similarities between SOCKS Proxies and HTTP Proxies
SOCKS and HTTP proxies are similar in the following ways:
- They are both based on internet protocols
Differences between SOCKS Proxies and HTTP Proxies
SOCKS and HTTP proxies differ in the following ways:
| SOCKS Proxies | HTTP Proxies | |
| Protocols | They support a large number of TCP protocols as well as UDP protocols | They only support HTTP and HTTPS protocols |
| Security | They do not encrypt data | HTTPS proxies encrypt data |
| Firewall Access | SOCKS proxies provide internet access through a network firewall | They do not provide a connection through firewalls |
| Data Interpretation | They do not interpret, analyze or rewrite data | They interpret data and, in some cases, rewrite the header packets |
| Interoperability | SOCKS proxies can use HTTP and HTTPS protocol | HTTP and HTTPS proxies cannot use the SOCKS protocol |
| OSI Classification | SOCKS proxies are found at a lower level (layer 5) of the OSI classification, i.e., the session layer | HTTP proxies are found on a higher level (layer 4) of the OSI classification, i.e., the transport layer |
| Configuration | SOCKS proxies can only be integrated into a web client or machine that is not a web server | HTTP proxies can be configured into either the web client or server |
| Port | SOCKS services are available through the SOCKS proxy ports 1080 and 1085 | HTTP proxies utilize ports 80, 8080, 8085, 3128, and 3129, while HTTPS proxies use port 443 |
SOCKS Proxy vs. VPNs
Granted, SOCKS proxies can create a secure tunnel through a firewall. But did you also know you can create a secure tunnel using a virtual private network or VPN? A VPN creates a secure route of communication between two networks: a local network and external networks. It achieves this by routing all internet traffic through a tunnel, but not before encrypting the data at the point of entry (your computer, for example). The tunnel terminates at an exit node (the VPN’s exit server) that assigns the outgoing requests from a user’s local network or computer a new IP address, effectively concealing the real IP address.
When using a VPN, all requests appear to originate from the exit note. At the same time, all responses from a web server appear to terminate at this VPN server. Thanks to this arrangement, you can use a VPN to access otherwise geo-blocked content of any location in which the VPN provider has a server.
For instance, if you are located in Germany and would like to access web content that is only viewable to residents in the United States, you can simply use a US-based VPN server.
To do this, you must first install VPN software on your computer, which will convert your machine into an entry node. The software is responsible for encrypting the data. Next, you will have to choose the exit node, and once the VPN connects to this exit server, you are free to send your request.
Advantages of VPNs
The pros of virtual private networks include:
- Encryption and security: VPNs encrypt all requests and server responses, thus guaranteeing unmatched security. It is for this reason that you are advised to use a VPN whenever accessing the internet through public Wi-Fi
- Provide access to geo-blocked content: A VPN virtually transports you to that location by routing traffic through an exit node in a different country. As a result, you can access web content that you would otherwise not have been able to in your home country without the VPN.
- Online privacy: VPNs hide your real IP address and subsequently assign a different address. This way, they protect your online privacy by concealing certain data about you, such as your location (state, city, country, and approximate coordinates).
Disadvantages of VPNs
The cons of virtual private networks include:
- Slow connection speeds: Because this solution has to encrypt all outgoing requests and incoming responses, it is usually slower.
- Logging user data: Another common downside that has led to uproar among VPN users is that some VPN providers often log user data. They do this in order to subsequently furnish law enforcement officials with the said data when prompted. In fact, several providers have made headlines by furnishing investigation bodies with user data. Moreover, some countries, such as India, have laws mandating VPN providers to save user data. Against this backdrop, observers have previously advised users to take providers’ ‘No logs’ policy at face value.
- Free VPNs are generally unsafe: Such VPNs often share the same secure tunnel among multiple users, which can increase the chances of ‘sniffing’ or eavesdropping.
- VPNs are banned in certain countries: some countries have made the use of VPNs outright illegal. In other nations, only government-licensed VPNs can be used.
Uses of VPNs
Virtual private networks are used in the following ways:
- VPNs provide security when accessing the internet through public access points
- Accessing geo-blocked content: as stated, VPNs, like SOCKS5 proxies, allow you to access any content from any location
- Facilitate remote work: companies safeguard their data by requiring their remote workers to log into their systems or servers through dedicated VPNs
How do SOCKS Proxies Compare to VPNs
Recalling the above-mentioned features, advantages, and disadvantages of SOCKS proxies, how do SOCKS proxies vs. VPNs compare?
Similarities between SOCKS Proxies and VPNs
SOCKS proxies and VPNs bear certain similarities, including:
- Online privacy: SOCKS5 proxies and VPNs conceal real IP addresses, thus offering online privacy
- Security: both solutions boost security, albeit in different ways. VPNs encrypt the data while SOCKS5 proxies perform authentication.
- Supported protocols: some VPN protocols, such as OpenVPN, support TCP and UDP, while SOCKS5 proxies also support TCP and UDP.
- Bypassing geo-restrictions: SOCKS5 proxies and VPNs can be used to access otherwise geo-blocked content.
Differences between SOCKS Proxies and VPNs
SOCKS proxy servers and VPNs differ in a few ways. The table below summarizes these differences:
| SOCKS Proxies | VPNs | |
| Protocols | SOCKS proxies, especially SOCKS5 proxies, support transport and application layer proxies, including FTP, SMTP, TELNET, HTTP, GOPHER, NTP, DHCP, BOOTP, NNP, TFTP, RTSP, RIP, and DNS | VPNs generally use VPN protocols such as IKEv2, OpenVPN, L2TP/IPSec, WireGuard, SSTP, and PPTP |
| Connection Speed | SOCKS proxies are generally faster because they do not undertake encryption | VPNs are slow because they encrypt data |
| Number of Servers | SOCKS proxy service providers often provide hundreds of thousands or even a couple of million proxy servers | VPN providers usually have fewer servers |
| Countries | Some SOCKS providers have proxy servers in over 150 countries | VPN providers usually have VPN servers in fewer countries, often less than 100 |
Conclusion
A SOCKS proxy enables communication between users’ computers as well as between web clients and web servers through a network firewall. Based on the SOCKS protocol, this proxy type prevents intruders from accessing the communication between the various parties. Over the years, the SOCKS protocol has been improved, resulting in several versions, namely SOCKS4, SOCKS4a, and SOCKS5. As a result, there are several types of SOCKS proxies, namely SOCKS4 proxies and SOCKS5 proxies, with the latter offering superior capabilities. SOCKS proxies are used in a number of ways, including torrenting, emailing, video streaming, live calls, and general browsing. They also provide online anonymity. In this article, we have compared SOCKS proxies to VPNs and HTTP proxies, and we hope you are better informed on which to choose for your unique needs.